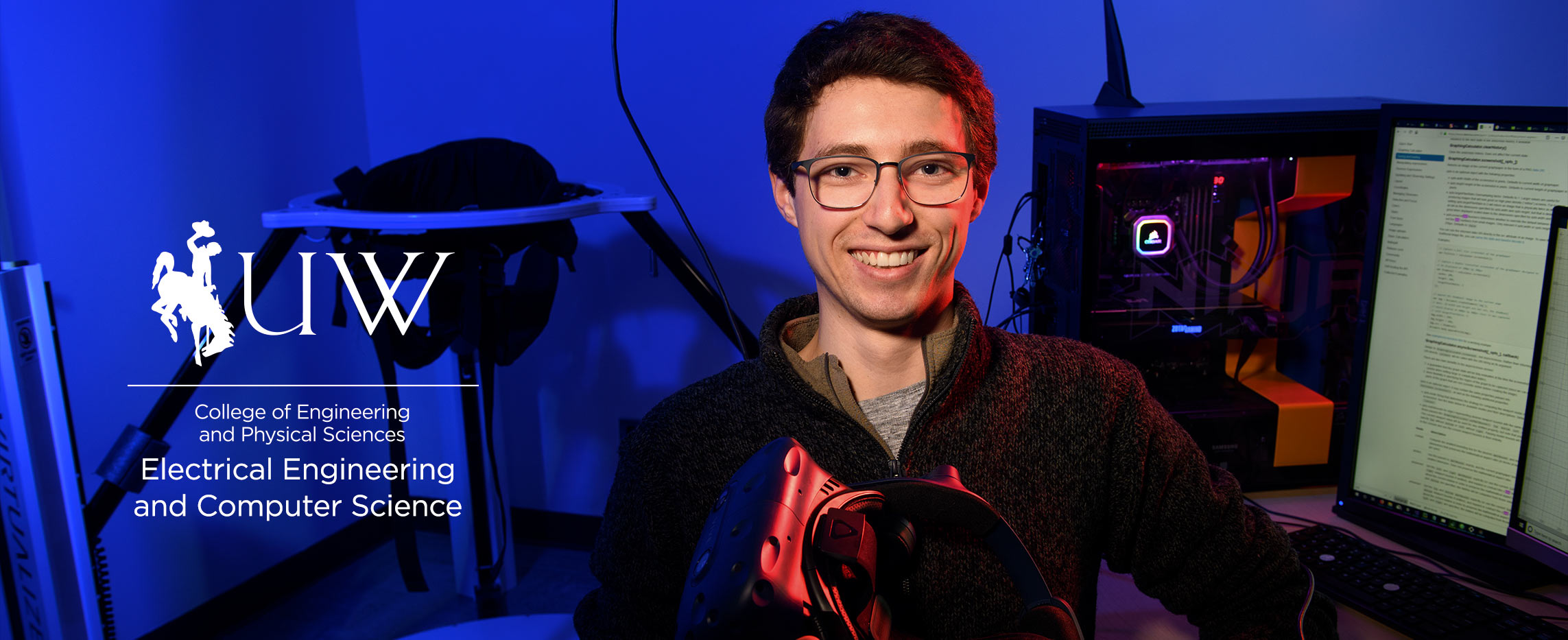

Equipping students and pursuing deeper understandings to create innovative software and technologies to better Wyoming and the world.
Faculty and Assistant Lecturer Positions in Computer Science
The College of Engineering and Physical Sciences (CEPS) of the University of Wyoming includes 10 departments and the newly formed School of Computing. The College prides itself on research innovation, teaching excellence, industrial engagement, and broader societal impact. With a significantly increased budget, we have embarked on a transformational journey to become a Tier-1 Institution, recognized nationally for academic excellence and world-class research. This includes new state-of-the-art facilities and dedicated funding for research initiatives. We are hiring a cohort of new faculty across the College, and we seek to attract a diverse and inclusive group of talented early-stage faculty and established researchers.
The Electrical Engineering and Computer Science department at the University of Wyoming seeks outstanding applicants for
An Assistant Lecturer/Instructional Professor in Computer Science, two tenure-track Assistant Professors in Cybersecurity, a tenure-track Assistant Professor in Statistical Signal Processing and Applications in Power Engineering, and a tenure-track Assistant Professor in Quantum Information Science and Engineering (QISE). More details, and a link to apply for the positions can be found at the respective links below:
https://eeik.fa.us2.oraclecloud.com/hcmUI/CandidateExperience/en/sites/CX_1/job/233975

Electrical Engineers design control and communication systems, sensors, displays,
machine learning , robots, instruments, speech recognition, computer vision, electronics,
motors, power systems, the internet of things—the list goes on and on.
UNDERGRADUATE PROGRAMS »
M.S. PLAN A PROGRAM »
M.S. PLAN B PROGRAM »
PH.D. PROGRAM »

Computer Engineering is a blend of Computer Science and Electrical Engineering. Computer
Engineering degree consists of both hardware and software courses.
UNDERGRADUATE PROGRAMS »

Traditional areas of computer science such as graphics, software engineering, networks,
databases, multimedia, and artificial intelligence remain strong, with job growth
being driven by the fundamental impact of computer science in nearly every industry.
UNDERGRADUATE PROGRAMS »
M.S. PLAN A PROGRAM »
M.S. PLAN B PROGRAM »
PH.D. PROGRAM »
1000 E. University Ave., Laramie, WY 82071
EN 5068 | Dept. 3295
Phone: (307)-766-2279
Email: eecs@uwyo.edu