CEDAR Symposium 2021
October 4, 2021
Malware Analysis at Scale with ElasticSearch
 |
Authors: Taylor McCampbell, Rafer Cooley Project Lead: Rafer Cooley Advisor: Dr. Mike Borowczak Abstract: With the exponential increase of malware being released every day, an efficient and resilient scheme for malware indicators is needed. To store, analyze, and develop future indicators, an efficient data management system is needed that can handle the amount of information necessary to accurately test said indicator schemes. This project continues work on the ARTEMIS project which investigates researchers can base protection for digital systems off techniques used by biological immune system |
Great Revolt: Attacking AI Models for Vulnerability Analysis
 |
Authors: Taylor McCampbell, Rafer Cooley Project Lead: Rafer Cooley Advisor: Dr. Mike Borowczak Abstract: Great Revolt is a large-scale project investigating the security of Machine Learning systems and infrastructure. Instead of focusing on the models themselves, it examines the underlying libraries and code that’s running those models. There are two phases to the Great Revolt project. First, research is being conducted on the artificial intelligence and machine learning fields to determine what types of modes are popular, what libraries do industry leaders use, and what hardware is machine learning typically ran on. Then, different AI/ML models will be analyzed from an adversarial standpoint to discover and test different vulnerabilities in industry standard models. |
Hermes: Developing Novel Attacks
 |
Authors: Clay Carper Project Lead: Clay Carper Advisor: Dr. Mike Borowczak Abstract: The most secure way to currently store private keys associated with cryptocurrency wallets is utilizing a hardware wallet, also known as a cold wallet. There is a variety of devices available, ranging from open source to privately managed. Each device has a unique recovery phrase which allows for recovery of private keys, should the device be lost or damaged. Accessing this recovery phrase presents an interesting and highly lucrative attack target. This project examines past known attacks at a hardware level and works to develop novel attacks against the entire class of devices. Improving the developer accessibility to potential side-channel threats is also desirable. |
Industrial Control System Outreach Training Development
 |
Authors: Michael Pate, Taylor McCampbell, Taylor LaForce Project Lead: Rafer Cooley Advisor: Dr. Mike Borowczak Abstract: Out-of-date and rarely updated computing devices control critical infrastructure systems such as power and water distribution. These devices often are complicated to update and patch for vulnerabilities since they control processes that are difficult or costly to stop. When connected to the internet, these devices pose a security risk which (if exploited) could harm the critical processes they are controlling. This research currently focuses on ICS outreach training development. Most training and education usually focus on regular cyber security skills. Our group is building modules that focus on training people for critical infrastructure security based on specific skill sets including awareness of everyday ICS and how they become compromised, programmable logic controllers and communication in control systems, and how to mitigate attacks on critical infrastructure.
|
Jangseung: Defense Against Adversarial Perturbations
 |
Authors: Alicia Thoney, Shawna Wolf Project Lead: Shaya Wolf Advisor: Dr. Mike Borowczak Abstract: Jangseung is a preprocessor that limits the effects of poisoning attacks without impeding on accuracy. Jangseung was created to guard support vector machines (SVMs) from poisoned data by utilizing anomaly detection algorithms. It was tested on a series of SVMs and protected them from basic poisoning attacks. Also, while Jangseung protects against adversaries actively attacking the accuracy of an SVM, it also defends against accidental false data that would otherwise go unnoticed and unintentionally poison an SVM. Current research is extending this to deep learning neural networks, different types of adversarial perturbations, and larger datasets for more complicated classification techniques.
|
Julia: A New Course with a New Language
 |
Authors: Danny Radosevich Project Lead: Danny Radosevich Advisor: Dr. Mike Borowczak Abstract: Universities across the country struggle to teach cohesive introductory computer science
courses that both invite new students to the field as well as motivate the use of
cultivated skills in other departments and majors. At the University of Wyoming, many
different departments teach their own versions of “Intro to CS”; however, each class
has low enrollment and/or outdated languages. The current approach to providing these
crucial skills to students wastes resources on antiquated course designs that fail
to teach students with the use of cutting-edge languages. This research develops a
flexible and intuitive introductory computer science course based on educational standards
as well as accessibility to students across many departments. This course was centered
around the Julia programming language and expands on areas that students from many
backgrounds can use moving forward.
|
Michelangelo: An AI Sculptor of Emergent Behavior
 |
Authors: Jenna Goodrich, Ally Hays, Taylor LaForce Project Lead: Andey Robins Advisor: Dr. Mike Borowczak Abstract: Michelangelo is a project, still in the inception phase, that seeks to bring self-learning,
genetic learning algorithms to distributed systems applications. These self-designing
systems emulate previous behavior as discovered in SHARKS research before generalizing
and creating more advanced and unresearched swarm systems. This project also has the
goal of making the design outputs of machine learning systems human-readable through
applied inductive program synthesis on a decentral-first domain-specific language.
Currently, this research focuses on two central questions. First, can we use genetic
learning and inductive program synthesis to develop an AI to sculpt intended emergent
behavior in decentralized and distributed systems. Second, what methods of selection,
crossover, and mutation should be used on the bytecode genes to create a genetic algorithm
that teaches these desired behaviors.
|
Orpheus: Prudent Vocal Authentication
 |
Authors: Shawna Wolf, Natasha Miller, Quinn Clark Project Lead: Shaya Wolf Advisor: Dr. Mike Borowczak Abstract: Orpheus is a prudent vocal authentication program that strives to preserve users’
privacy while storing vocal data for user verification. Current speaker recognition
systems pose security threats because vocal feature data can be used to reproduce
a person’s unique voice, which can compromise a system or expose a user’s private
biometric data. Currently, the Orpheus group is building a privacy framework and constructing
machine learning models for vocal authentication that measure the amount of biometric
data leaked by each model. So far, scripts have been developed to record audio and
extract features commonly used in vocal authentication models (utilizing the Librosa
Python library). Next, models will be constructed and measured against our privacy
metric to determine which models and datasets pose the least danger to user privacy.
|
CEDAR Summer Outreach Camps and Programs
 |
Authors: Mason Johnson, Danny Radosevich, Andey Robins Project Lead: Mason Johnson Advisor: Dr. Mike Borowczak Abstract: The development of a Cybersecurity and Computer Science pipeline begins in K-12 classrooms.
The CEDAR center provides a variety of professional development and summer camp experiences
funded by various federal agencies (e.g., NSF, NSA) and corporate sponsors (e.g.,
MilliporeSigma, Kraken). In 2021 these activities reached more than 150 K-12 teachers
and students while also providing University of Wyoming students with relevant communication,
teaching, and research experiences. You can find out more about the variety of opportunities
at the University of Wyoming Computer Science Hub located online at https://www.uwyo.edu/WyCS
|
CEDAR PacMan: Maze Authentication Using Behavioral Biometrics
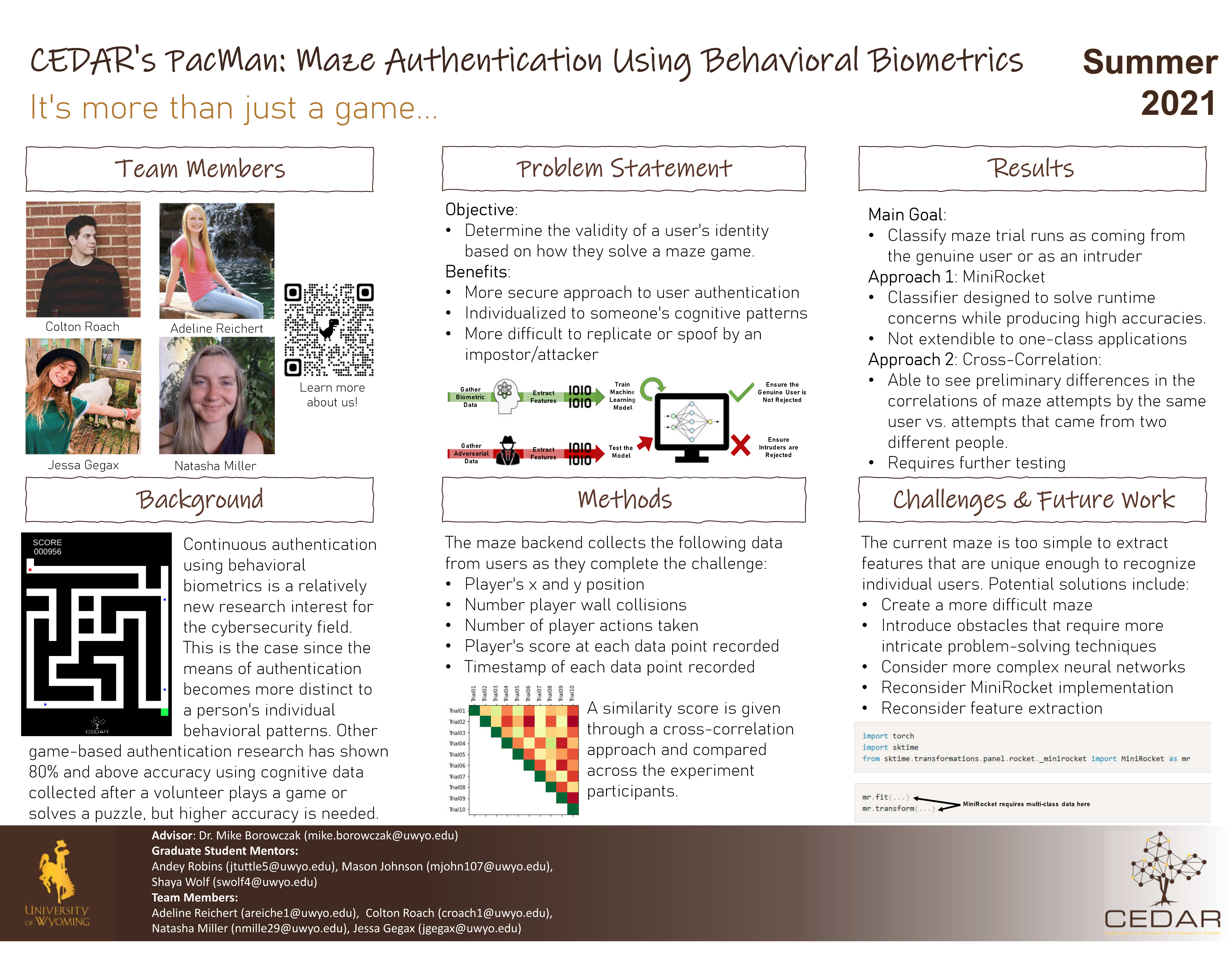 |
Authors: Colton Roach, Adeline Reichert, Jessa Gegax, Natasha Miller Project Lead: Shaya Wolf, Mason Johnson, Andey Robins Advisor: Dr. Mike Borowczak Abstract: PacMan is an authentication mechanism built around how a user completes a puzzle,
in this case a simple, randomly generated maze. Other game-based authentication research
has shown around 80% accuracy using cognitive data, but higher accuracy is needed
before such models could be utilized in real-world environments. Current attempts
revolve around making puzzles/mazes that are complex enough to ensure user behavior
is unique, but simple enough that it is not an arduous task. Our group has looked
at two approaches for validating users with high accuracy. First, the MiniRocket model
was considered given the models ability to solve runtime concerns and produce high
accuracies; however, this model is not built for one-class classification problems.
Second, cross-correlation statistics were used to see preliminary differences in how
a user completes a maze versus how others attempt the same problem.
|
Secret-Agent: Behavioral-Biometric Continuous Authentication
 |
Authors: Jarek Brown, Faith Coslett, Adeline Reichert Project Lead: Shaya Wolf, Danny Radosevich Advisor: Dr. Mike Borowczak Abstract: This research spoofs continuous authentication models using algorithms that utilize
limited user data to mimic their biometrics. Spy Hunter, a continuous authentication
mechanism uses keystroke dynamics to validate users over blocks of data. This easily
incorporated periodic biometric authentication system validates genuine users and
detects intruders using keystroke dynamics. Currently, SecretAgent uses keystroke
timings gathered for the SpyHunter authenticator and runs a simple algorithm to reconstruct
press and release times for the user. Then, a script takes an adversary’s typing pattern
and fires the key presses at the cadence of the valid user to spoof the authenticator.
|
SHARKS Obstacle Avoidance
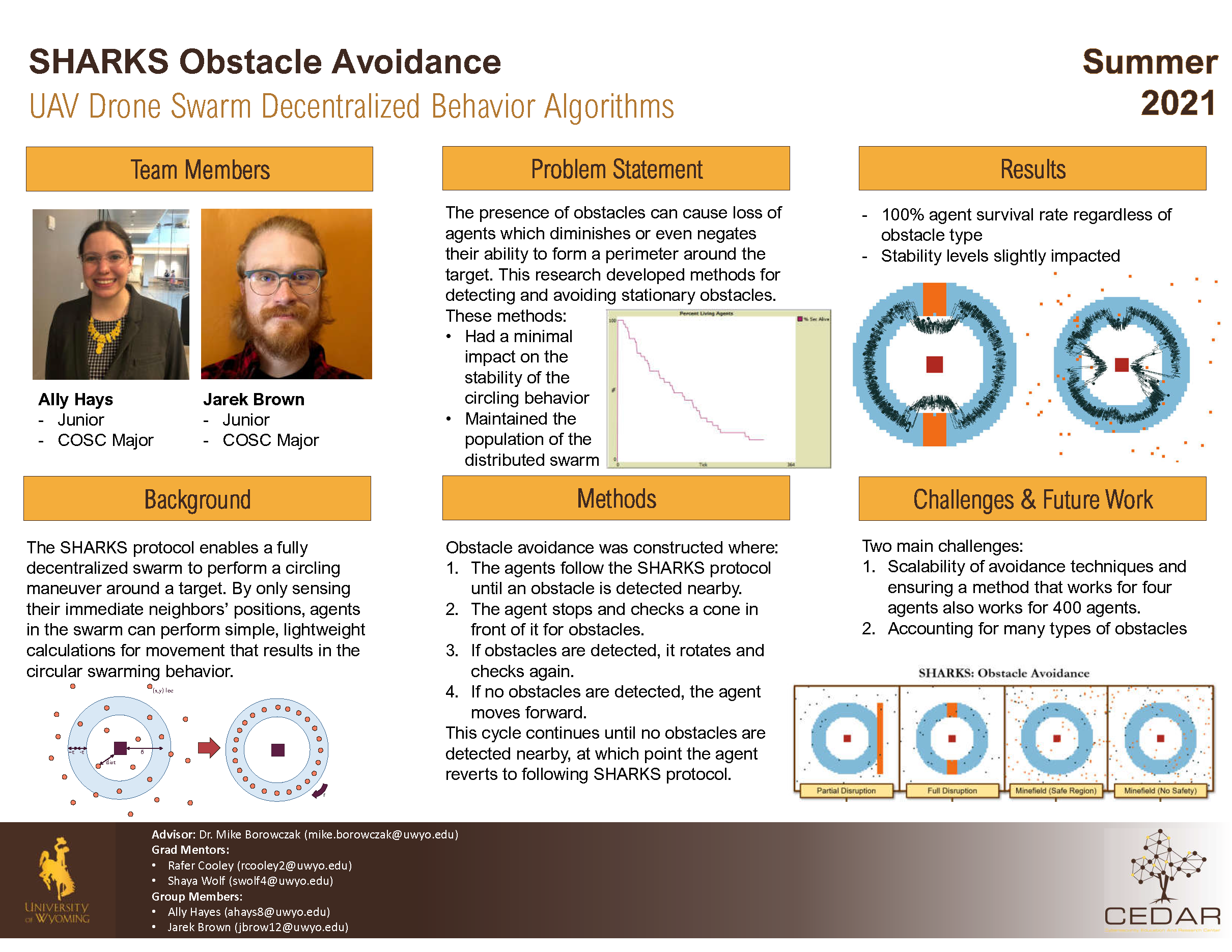 |
Authors: Ally Hays, Jarek Brown Project Lead: Rafer Cooley, Shaya Wolf Advisor: Dr. Mike Borowczak Abstract: The Secure, Heterogeneous, Autonomous, and Rotational Knowledge for Swarms (SHARKS)
protocol investigates distributed algorithms for swarm movement patterns. The drones
in any given swarm have restrained compute resources and little memory, so developing
efficient behaviors is necessary for the agents to work within these restrictions.
In addition to positioning behaviors, this project investigates safety protocols to
protect the swarm from adversarial swarms and environmental obstacles. Current research
focuses on four types of stationary obstacles that cause the swarm to die off. Different
avoidance techniques are tested and shown effective for maintaining the population;
however, the stability of the swarm is diminished.
|
Privacy Inference Under Side Channel Power Attacks
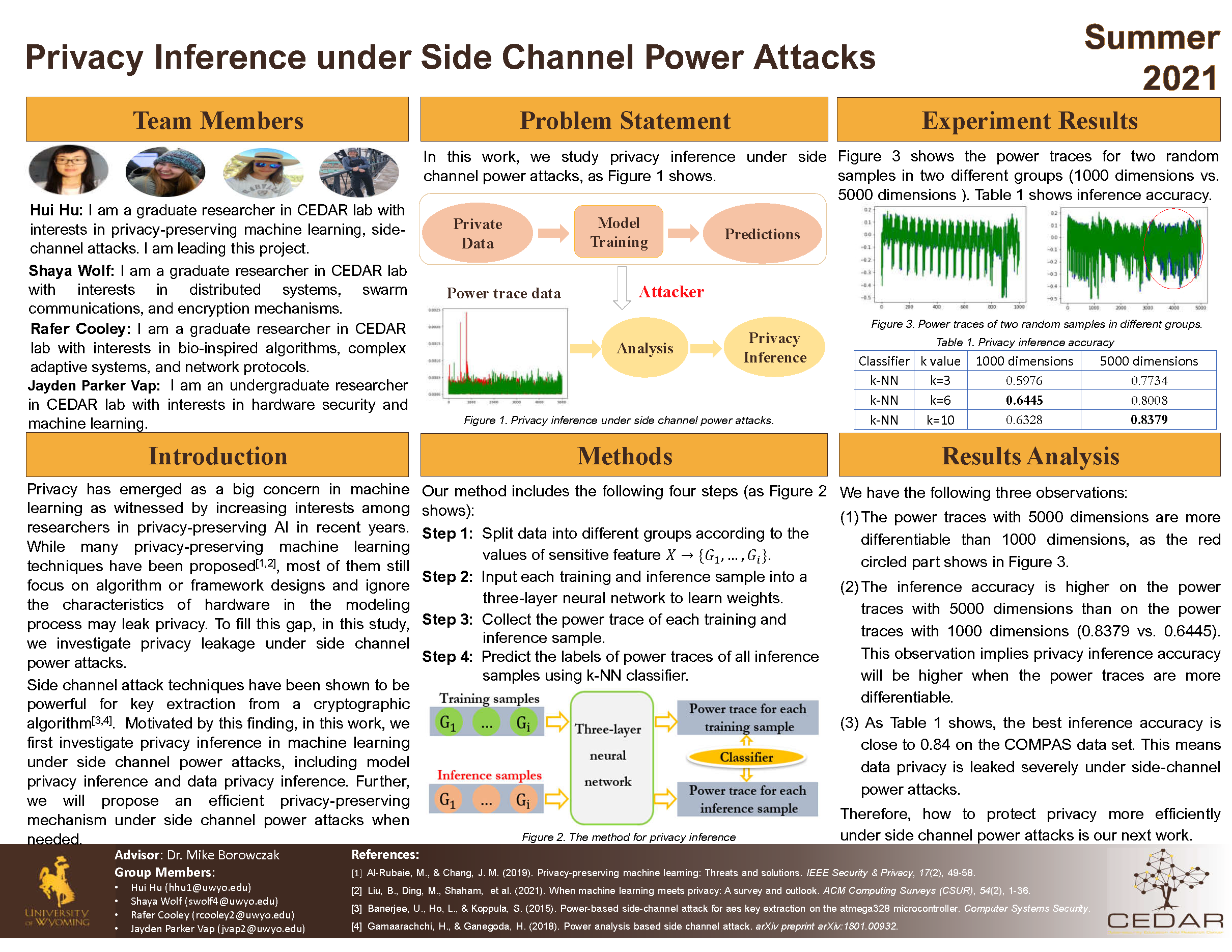 |
Authors: Hui Hu, Shaya Wolf, Rafer Cooley, Jayden Parker Vap Project Lead: Hui Hu Advisor: Dr. Mike Borowczak Abstract: This project aims to infer private user data by utilizing side-channel power attack
techniques on machine learning models deployed on dedicated hardware. This research
considers both model privacy and data privacy. Our previous studies have shown that
side-channel power attacks are efficient in inferring private information in the modeling
process such as model types, model structures, or model hyperparameters. This allows
an adversary to determine finer details about a model that are generally considered
private to protect the model from common machine learning attacks. Currently, we are
looking into adversarial sample detection and privacy-preserving under side-channel
power attacks. In other words, we consider attacks that allow us to infer sensitive
user data and ask how we may protect models from both of these attack vectors without
loss of model accuracy.
|
Offensive and Defensive Analysis of Behavioral Biometrics on Smart Wearables

